DNIF HYPERCLOUD
Cloud native SIEM, UEBA and SOAR built to discover threat campaigns and cut analyst overhead.
Built for customers with a large dataset who are finding existing SIEM platforms extremely expensive at scale.
Unbreak your Security Operations Center
Log everything
Maximize your logging capacity without fretting over costs—double, perhaps even triple your capacity with your existing budget.
With the HYPERCLOUD, the fear of overlooking crucial information is a thing of the past. Log everything, leave nothing behind.
Never rehydrate
By default, the HYPERCLOUD provides you with instant access to all your events for a full year. Trend threats and user behavior without resources.
Say goodbye to wasting time on restoring archives or requesting rehydration for threat hunting or forensic analysis of a reported IOC.
Responders' dream
CoDOTS empowers SOC teams to slash their on-screen time by 68%, eliminating the exhaustion caused by an overwhelming flood of alerts.
The HYPERCLOUD seamlessly connects threats, enabling you to focus exclusively on combating threat campaigns.
Is cost blocking your SIEM adoption?
New innovation in data storage, retrieval and aggregation brings a 90% reduction in cost.
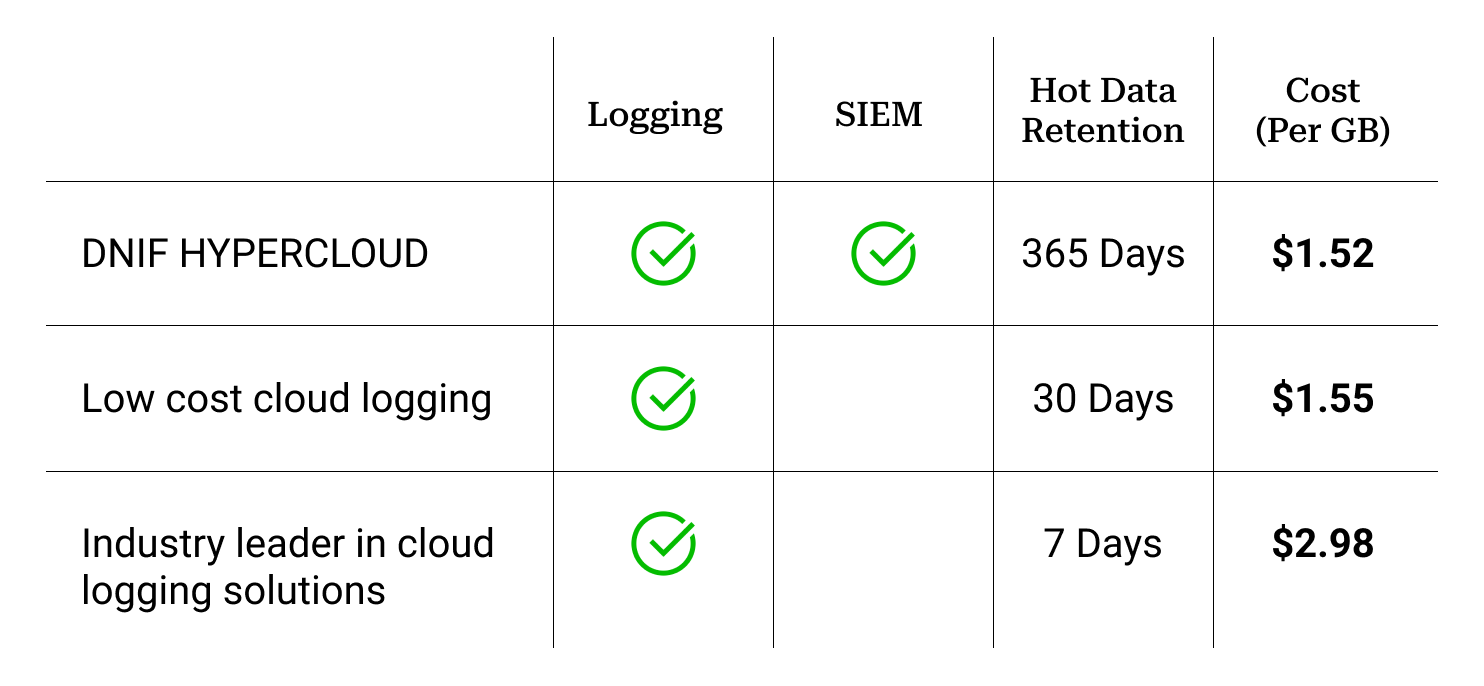
The HYPERCLOUD breaches all benchmarks and allows you to ingest everything and eliminate blind spots in your estate. Retain your data for longer, facilitate hunting, enable machine modeling and compliance.
Blog Post - Why cost is a barrier to good detection
Key Features You Will Love
Reduced Alert Fatigue
Connect the dots and retrace footsteps of threat actors. DNIF HYPERCLOUD uses cognitive machine learning and graph analytics to reduce hundreds of alerts down to a few threat campaigns.

MITRE ATT&CK® FRAMEWORK Alignment
Know what you can detect and what you can't. All threat content is mapped with the MITRE ATT&CK® framework. Case management will tell you campaign progression through the killchain.

Intuitive Search and Building Blocks
DNIF HYPERCLOUD provides the ability to query, search and build complex security analytics use cases using native query language or a simple GUI based query builder.
Use the power of pipelines much like python Jupyter notebooks.

there is more you will love...
Parse and extract fields from raw events at run time, apply retrospectively
There is nothing called Warm / Cold Storage, everything is HOT for 365 Days
Use pipelines to call in multiple logic blocks, create multi stage use cases
Families of use cases, constantly evolving to match the changing threat landscape
Connect to multiple cloud service providers and stream events in real-time
Out of the box content to detect outliers using no code machine learning
Like what you see?
Request a personalized demo to see how DNIF is better than your existing SIEM.
Work with EVERYTHING You Need
Seamless integration with security devices, operating systems, cloud workloads and applications.








Oh don't worry we have a lot more, check out our full list of integrations.
A Platform that you can TRUST
We make compliance a top priority for your organization and for ours. We have aligned our security controls and processes with industry best practices and work with third-party auditors to test our systems, controls, and processes regularly.



.png?width=300&name=netmonastery%20nspl%20(1).png)

Meet the Pioneers, Our Customers
Early investors who helped us move the needle, join this list





What's trending?
Stay ahead with our insights, best practices, and case studies to help redefine your threat detection strategies.
Real-World Use Cases of Comprehensive Logging with DNIF HYPERCLOUD
Start ReadingUnleash True Potential of Comprehensive Logging with DNIF HYPERCLOUD
Start ReadingThe Importance of Comprehensive Logging in Modern Cybersecurity
Start ReadingTATA CONSULTANCY SERVICES
"DNIF HYPERCLOUD has a library of UEBA models that are effective out of the box and also provides our data engineers the flexibility to develop custom ML / UEBA models that help reduce false positives in our fluid environment.
It was a great fit because of its ability to scale beyond 20TB per day with a minimal infrastructure footprint, without compromising on performance, retention or data resolution."

